Securing Data in the Modern Era: Essential Practices for 2025
In today’s interconnected world, data is the lifeblood of organizations and individuals alike. With the rapid advancement of technology, the need for robust data protection measures has never been more urgent. Effective data security is not just about protecting sensitive information; it’s also about maintaining trust, ensuring compliance with regulatory standards, and safeguarding an organization’s reputation. In 2025, as cyber threats become increasingly sophisticated, implementing comprehensive data security best practices is essential to mitigate risks and prevent breaches.
Understanding the Core Principles of Data Security
Data security involves a range of strategies and technologies designed to protect digital information from unauthorized access, use, disclosure, disruption, modification, or destruction. The primary goal is to ensure that data remains confidential, intact, and available to authorized users. To achieve this, organizations must adopt a multi-layered approach that includes both technical and administrative controls.
Classify Data by Sensitivity
One of the foundational steps in data security is classifying data based on its sensitivity. Not all data is created equal, and understanding the risk associated with different types of data is crucial. Organizations should categorize data into levels such as public, internal, confidential, and restricted. This classification helps determine the appropriate security controls needed for each type of data.
Enforce Least Privilege
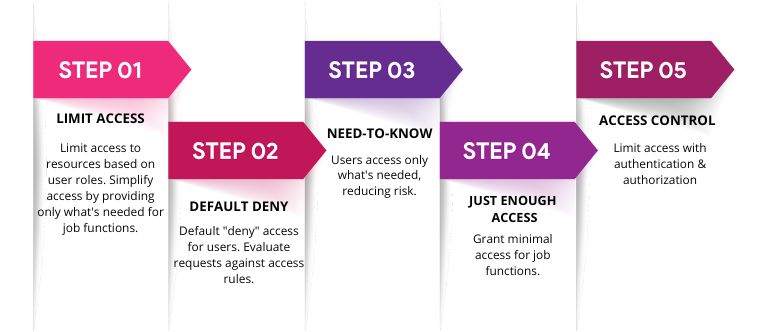
The principle of least privilege (PoLP) states that users should only have the minimum level of access necessary to perform their job functions. This reduces the risk of unauthorized access and limits the potential damage that could result from a breach. Implementing context-aware access control further enhances security by considering factors such as user roles, device posture, and location.
Advanced Techniques for Data Protection

Beyond basic access control, there are several advanced techniques that can significantly enhance data security. These include encryption, secure data storage, and continuous monitoring for suspicious activity.
Secure Data at Rest and in Transit
Data stored on physical media or in cloud environments must be protected through strong encryption. Encryption ensures that even if data is intercepted, it remains unreadable without the appropriate decryption key. Additionally, data in transit between systems should be secured using protocols like TLS to prevent eavesdropping and tampering.
Protect Against Inference and Aggregation Attacks
Inference and aggregation attacks pose a unique threat by allowing attackers to reconstruct sensitive information from seemingly innocuous data. To combat these attacks, organizations should implement query restrictions, noise injection, and multilevel security models. These measures help prevent the piecing together of low-risk data to uncover restricted information.
Building a Resilient Data Security Framework

A resilient data security framework ensures that systems can withstand disruptions and recover quickly from incidents. This involves designing systems with redundancy, implementing robust backup and recovery processes, and regularly testing these procedures.
Design for Resilience
Resilience is not just about preventing breaches; it’s also about ensuring that data remains accessible and usable after disruptions. Organizations should design systems with built-in redundancy, such as distributed storage and automatic failover mechanisms. Regularly testing recovery processes against recovery time objectives (RTO) and recovery point objectives (RPO) ensures that systems can bounce back efficiently.
Integrate Data Security into System Design

Integrating data security into system design from the outset is critical. This involves embedding security principles into the architecture of applications and infrastructure. By doing so, organizations can address potential vulnerabilities early and reduce the risk of architectural blind spots.
Compliance and Continuous Improvement
Compliance with industry regulations and standards is an essential aspect of data security. Frameworks such as the NIST Cybersecurity Framework and ISO/IEC 27001 provide structured approaches to managing cybersecurity risks. Organizations should also continuously review and update their security policies to adapt to evolving threats.
Use Established Cybersecurity Frameworks
Frameworks like the NIST Cybersecurity Framework offer a comprehensive approach to managing cybersecurity risks. They help organizations define categories and subcategories for protecting data and map their controls to recognized best practices. By leveraging these frameworks, organizations can ensure consistency in policy implementation and align with industry expectations.
Monitor and Improve Security Posture

Continuous monitoring and improvement of the security posture are vital for staying ahead of emerging threats. This includes regular audits, vulnerability assessments, and employee training programs. By fostering a culture of security awareness, organizations can better protect their data and respond effectively to incidents.
Conclusion
In 2025, the landscape of data security is more complex than ever. As organizations navigate this evolving environment, adopting a proactive and comprehensive approach to data protection is essential. By classifying data, enforcing least privilege, securing data at rest and in transit, and integrating security into system design, organizations can build a resilient defense against cyber threats. Furthermore, leveraging established frameworks and continuously improving security practices will ensure that data remains protected in an increasingly interconnected world.